Solved Exercise 1. (Candidate Encryption Schemes) Let se be
Por um escritor misterioso
Descrição
Answer to Solved Exercise 1. (Candidate Encryption Schemes) Let se be
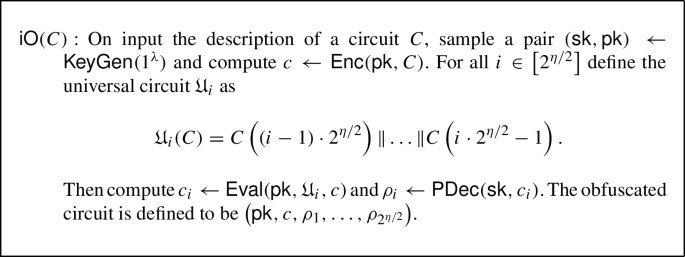
Candidate iO from Homomorphic Encryption Schemes

Strategizing AI-powered middleware system design for Human

Electronic voting systems for defending free will and resisting

Homomorphic Encryption — Theory and Application

COVID-19 Cybersecurity Alerts, Coronavirus Phishing Scam
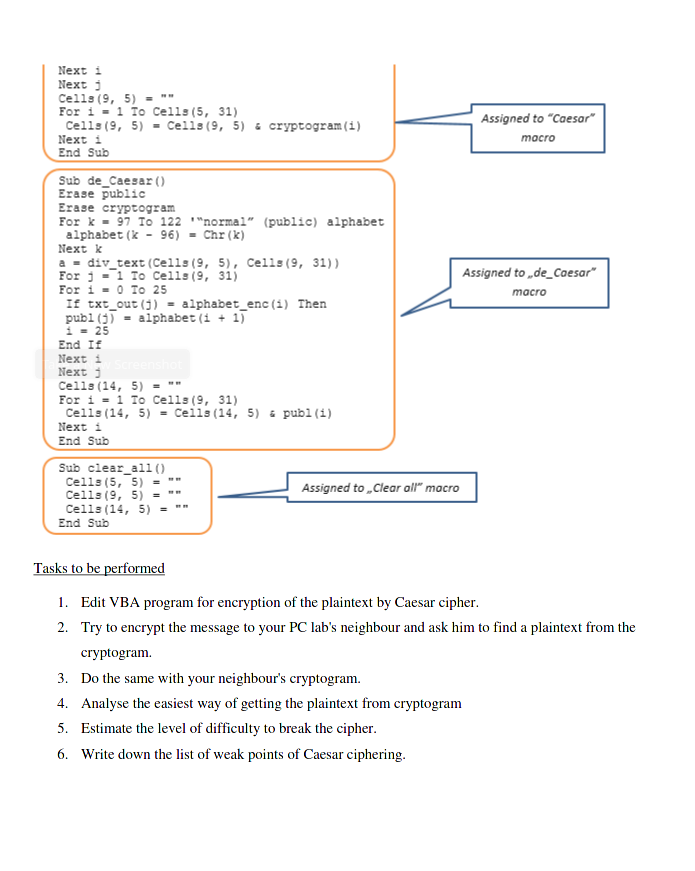
Introduction to Exercise 1 Symmetrical cryptography
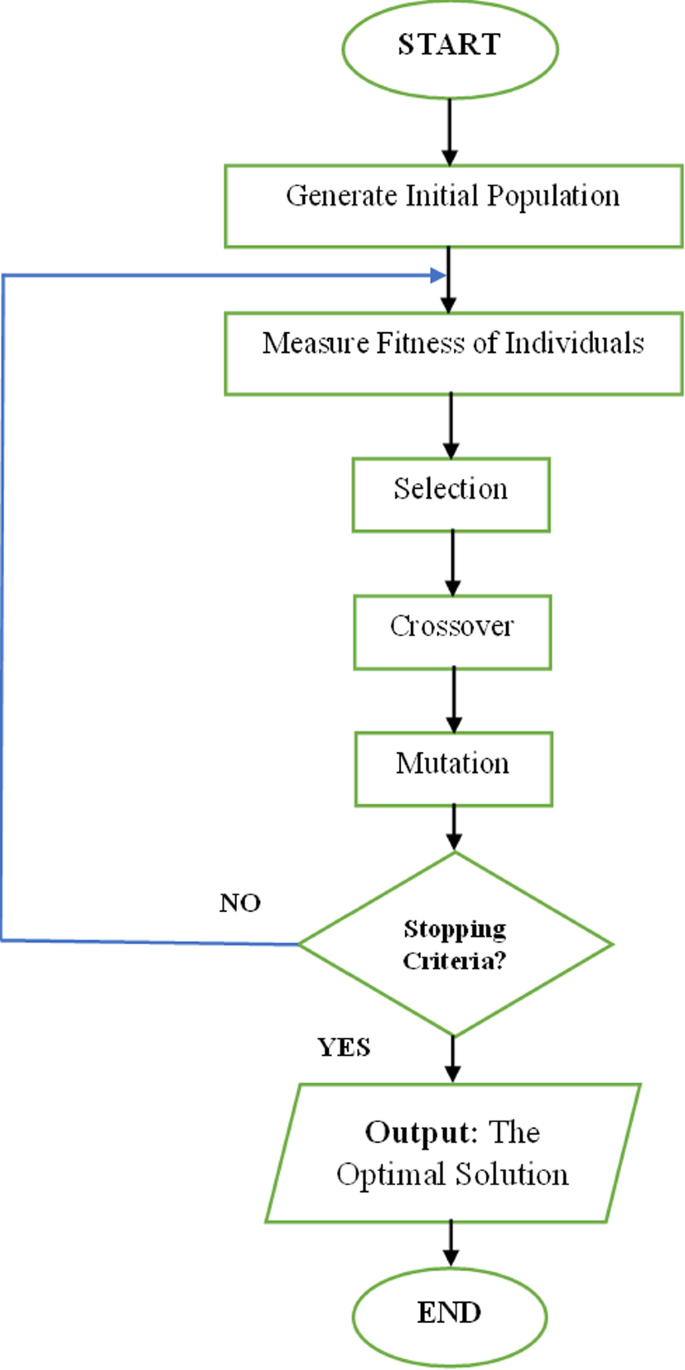
High-performance computing-enabled probabilistic framework for

Applied Sciences, Free Full-Text

Review of the Decomposition of Ammonia to Generate Hydrogen

An Introduction to Cryptography
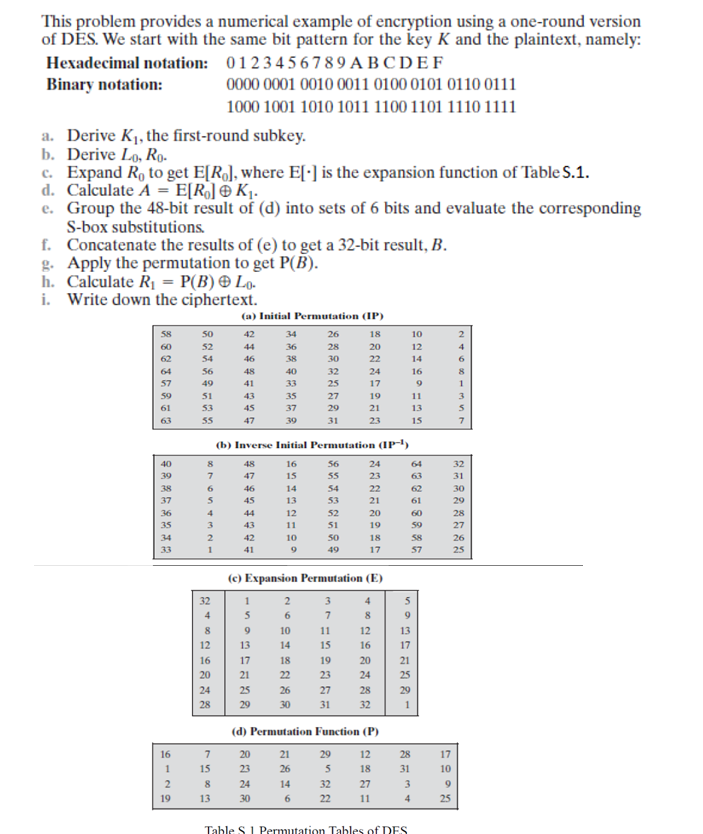
Solved This problem provides a numerical example of

Skin-Interfaced Wearable Sweat Sensors for Precision Medicine
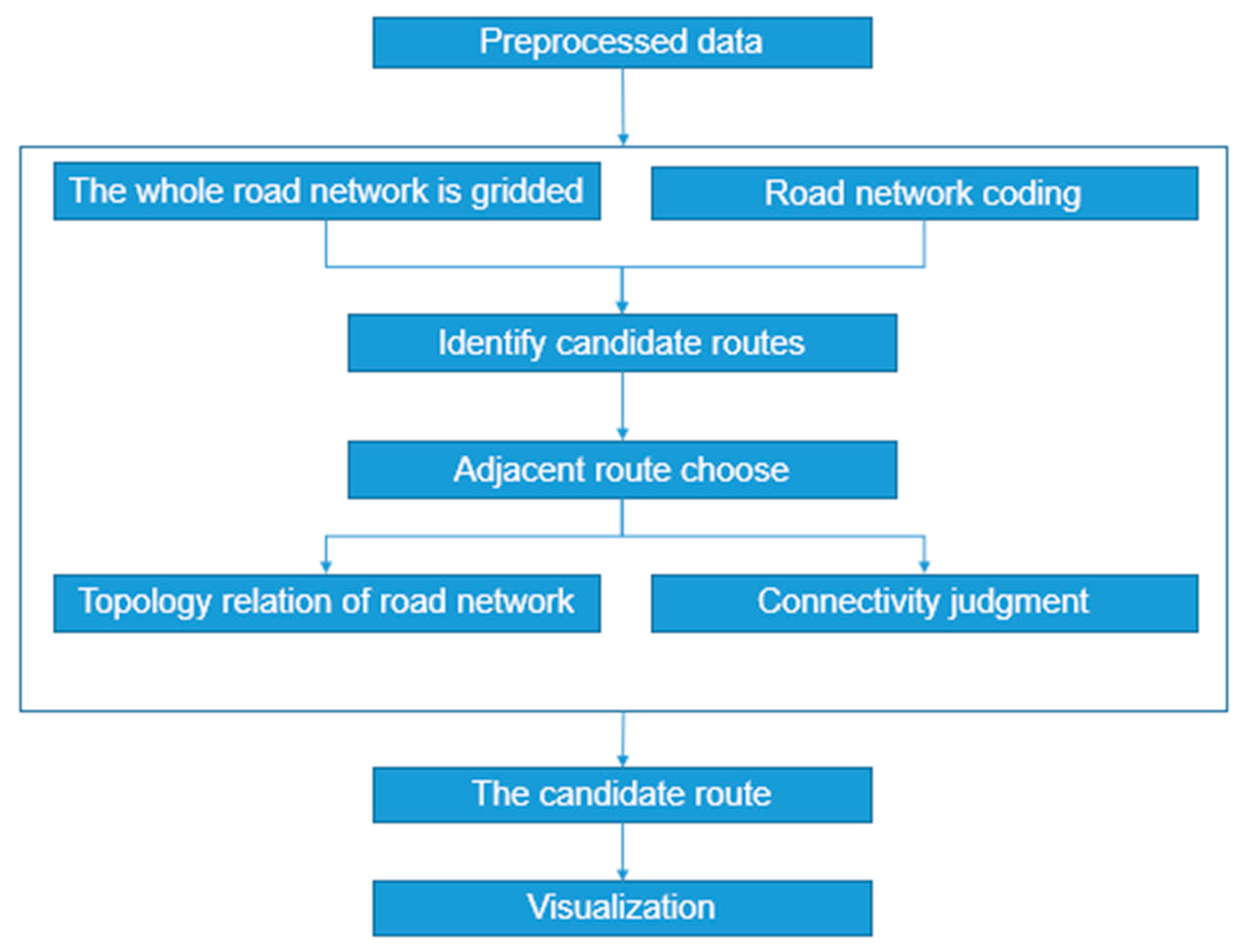
Sustainability, Free Full-Text
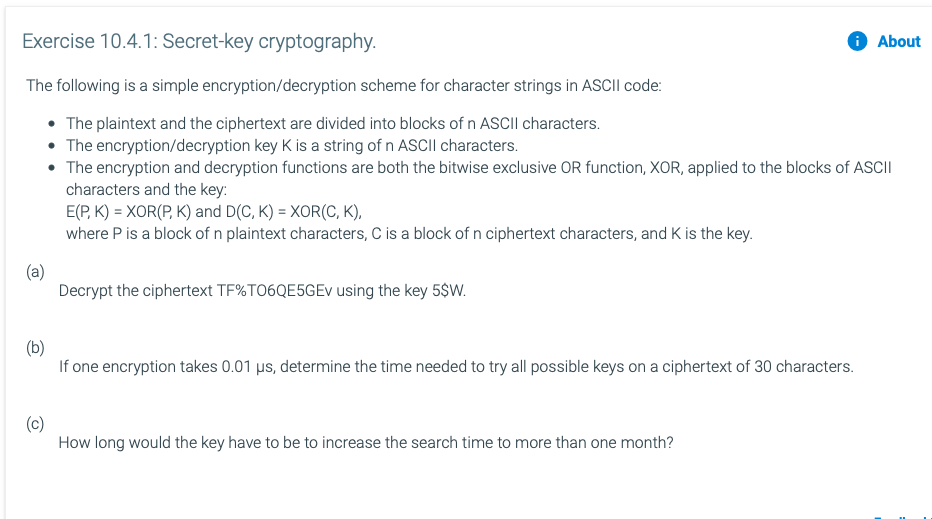
Solved Exercise 10.4.1: Secret-key cryptography. A About The
The post-quantum state: a taxonomy of challenges
de
por adulto (o preço varia de acordo com o tamanho do grupo)







