Hack Attacks Testing How to Conduct Your - Back to Home
Por um escritor misterioso
Descrição
Hack Attacks Testing How to Conduct Your - Back to Home

To Improve Cybersecurity, Think Like a Hacker

How Do Hackers Normally Get Caught?

spoiler alert attack simulation isnt ethical hacking
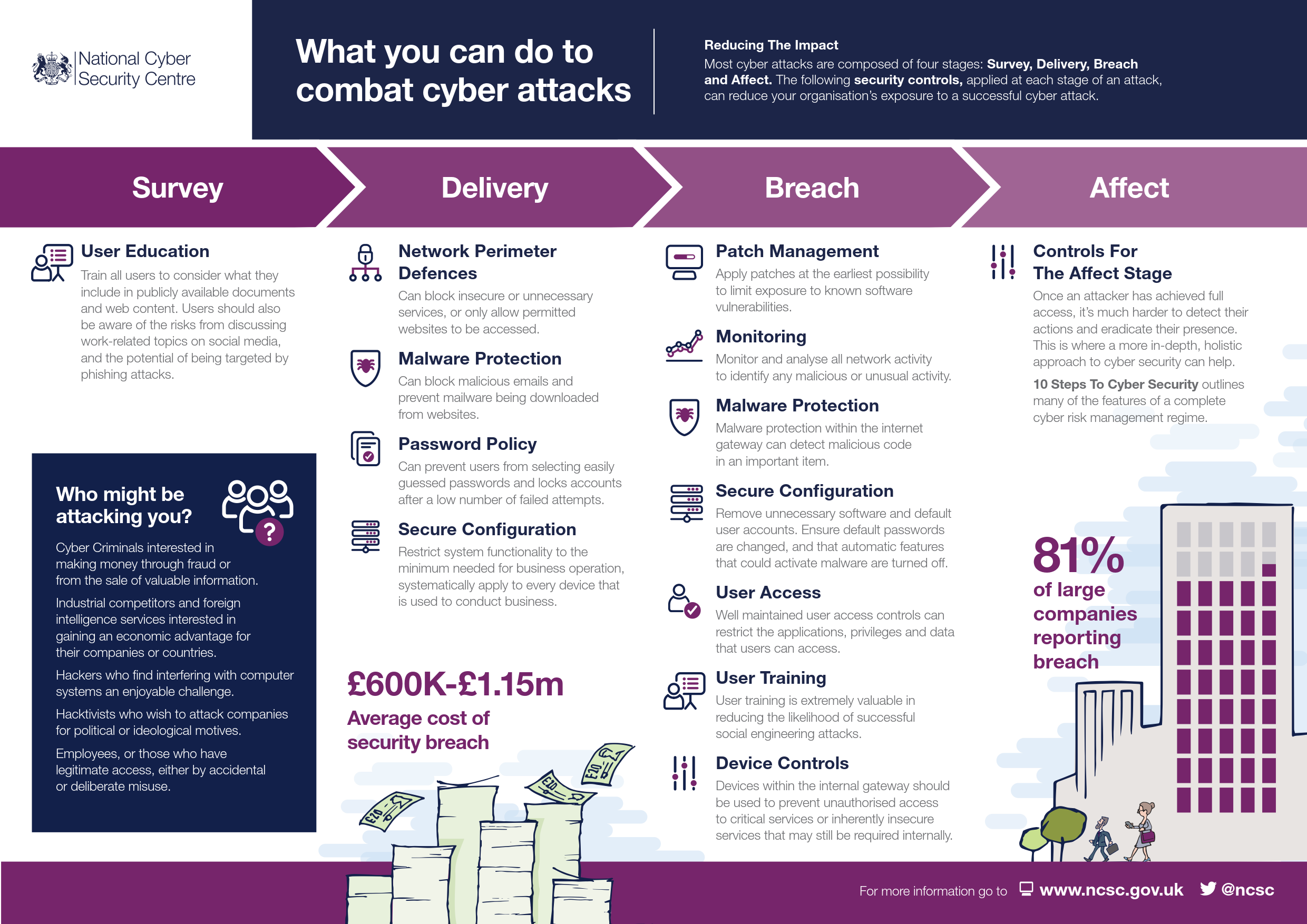
Reducing your exposure to cyber attack
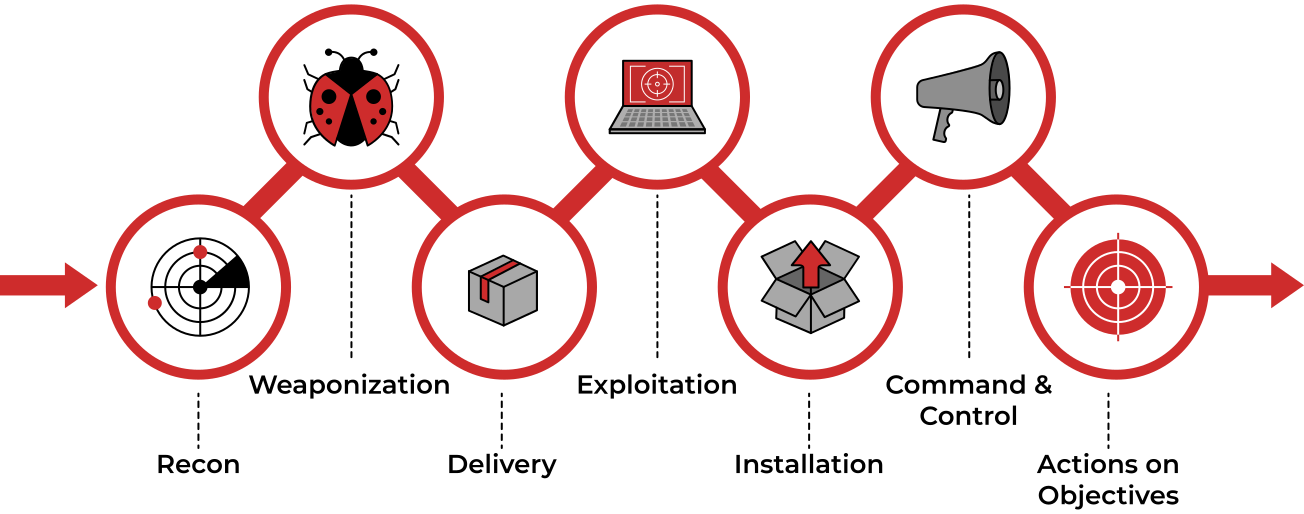
TryHackMe Cyber Kill Chain Room. The Cyber Kill Chain framework is…, by Haircutfish

6 Things You Need to Do to Prevent Getting Hacked
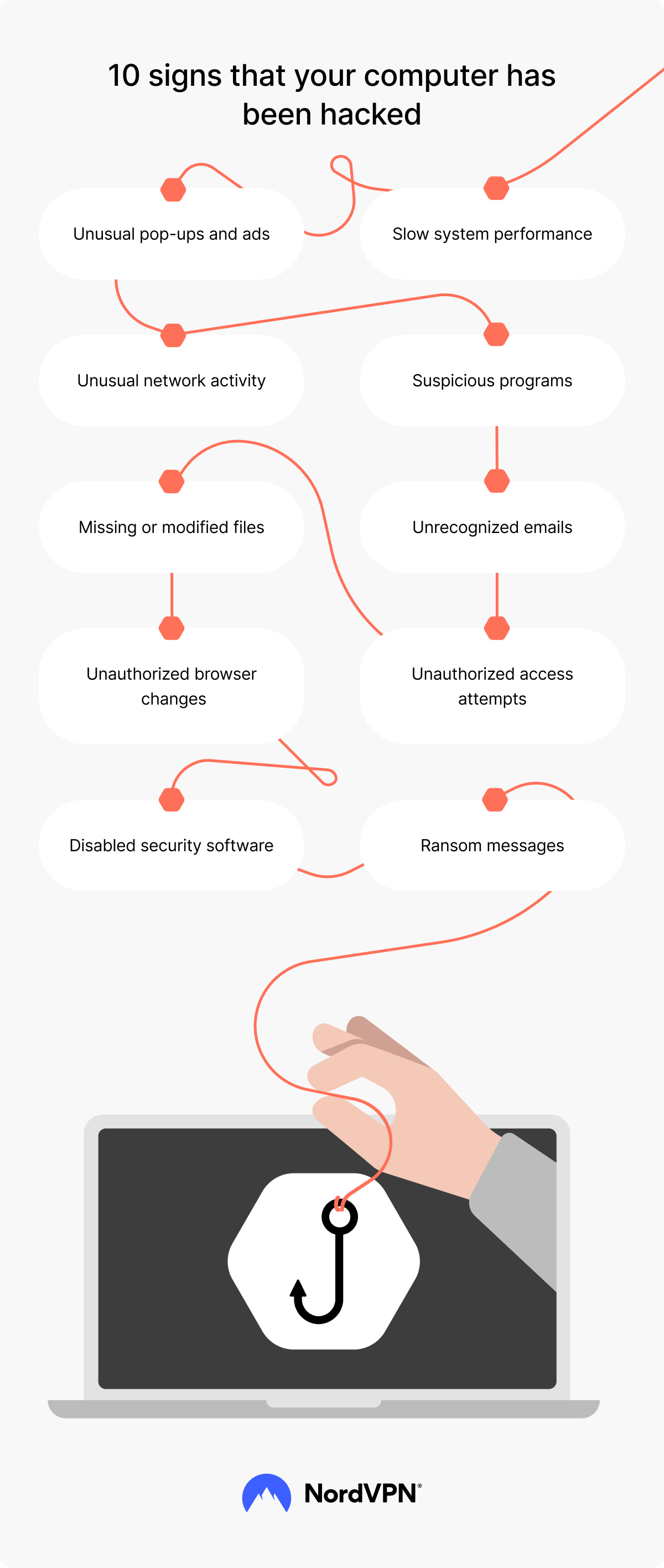
How to tell if your computer has been hacked
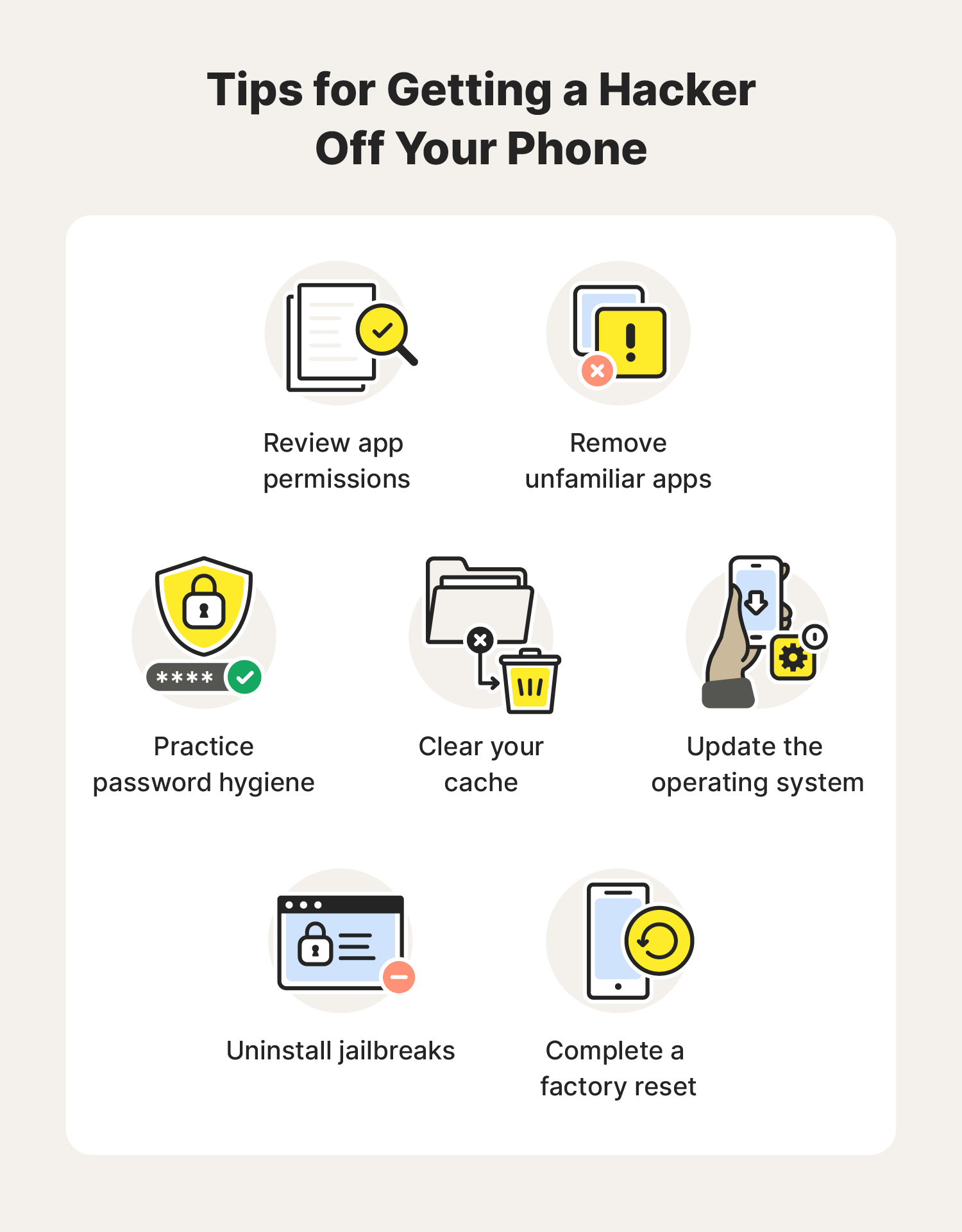
How to remove a hacker from my phone - Norton
What is Penetration Testing and How Does It Work?

What is Cybersecurity & Importance of Cyber Security

What you actually need to do if you're hacked - F-Secure Blog

What is Penetration Testing?: A [Step-by-Step] Guide
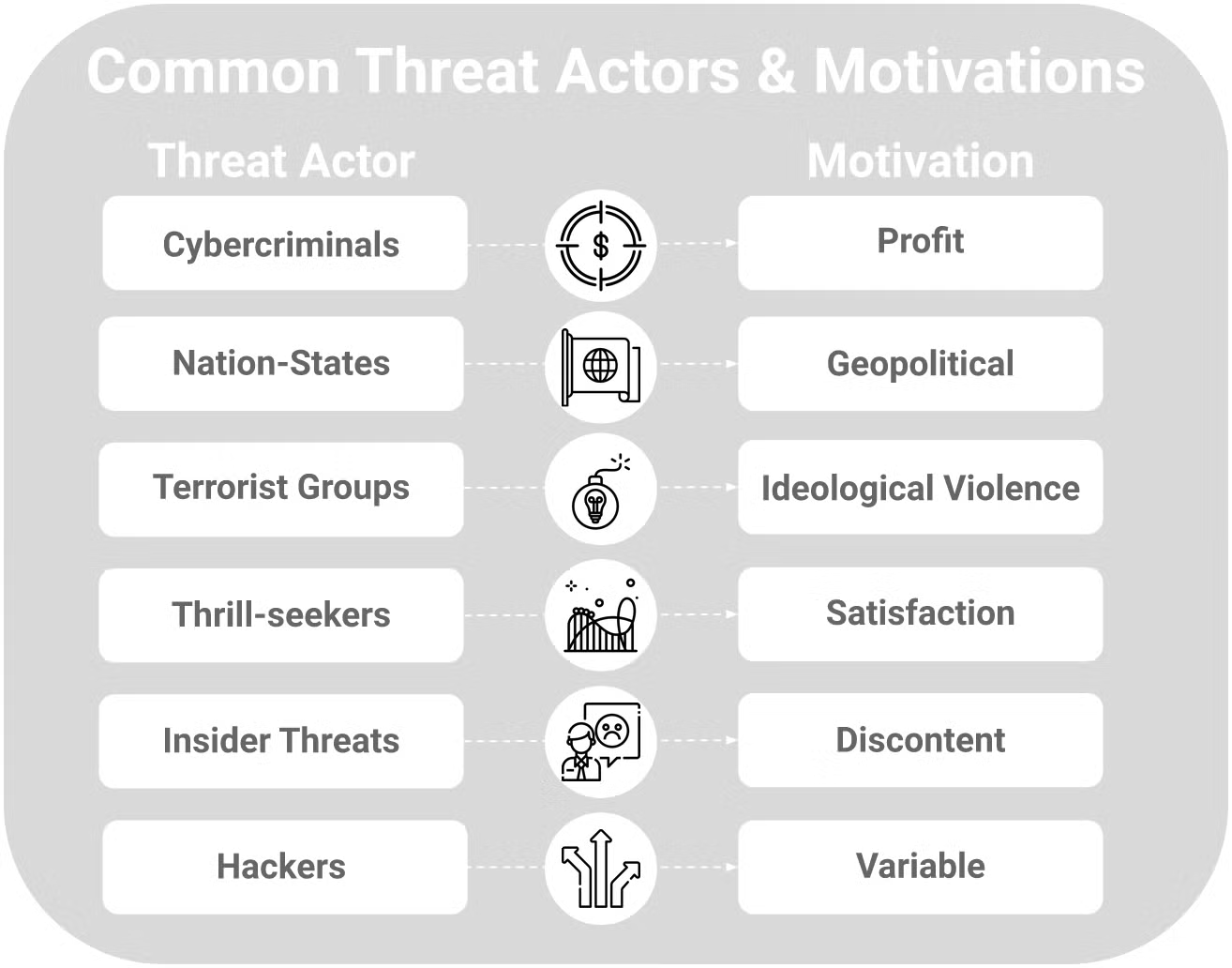
What is a Threat Actor? Types & Examples of Cyber Threat Actors

Complete Guide to Ransomware: How to Recover and Prevent an Attack
de
por adulto (o preço varia de acordo com o tamanho do grupo)