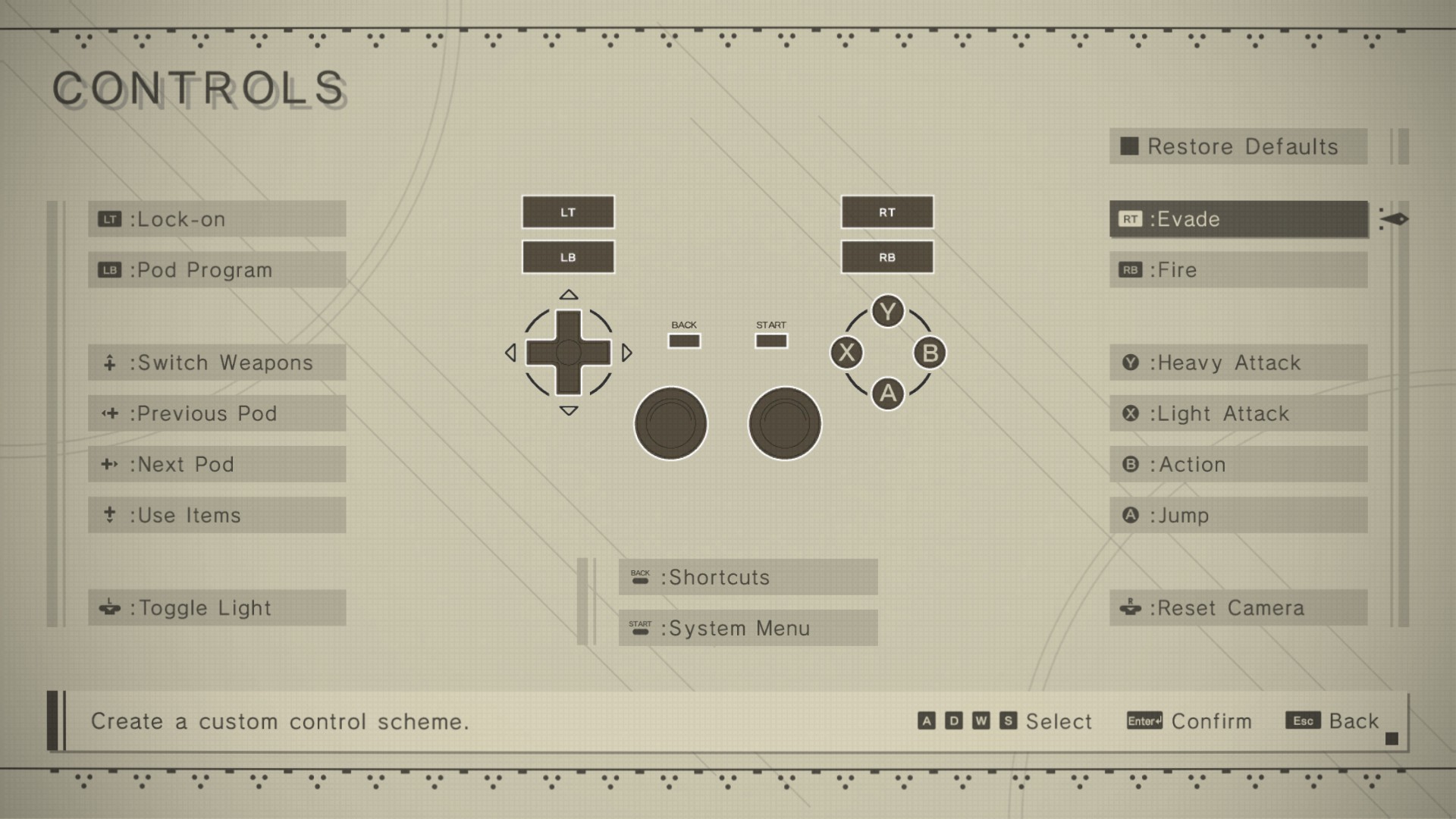
Suspicious User Controls
Por um escritor misterioso
Descrição

Foxit Reader Crash Report with Suspicious Registry Change Request – Help Center
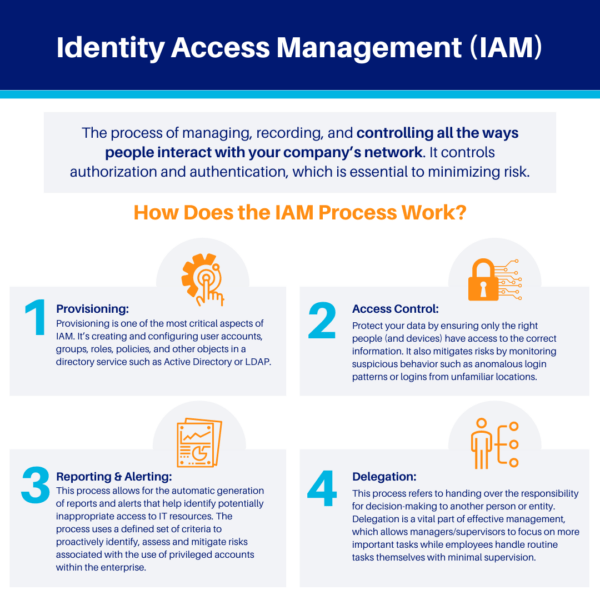
Overview of Identity Access Management (IAM)
Taking Back Control of Your SOC with Risk Based Alerting

Report Suspicious Activity & Fraud Alert for Azure MFA
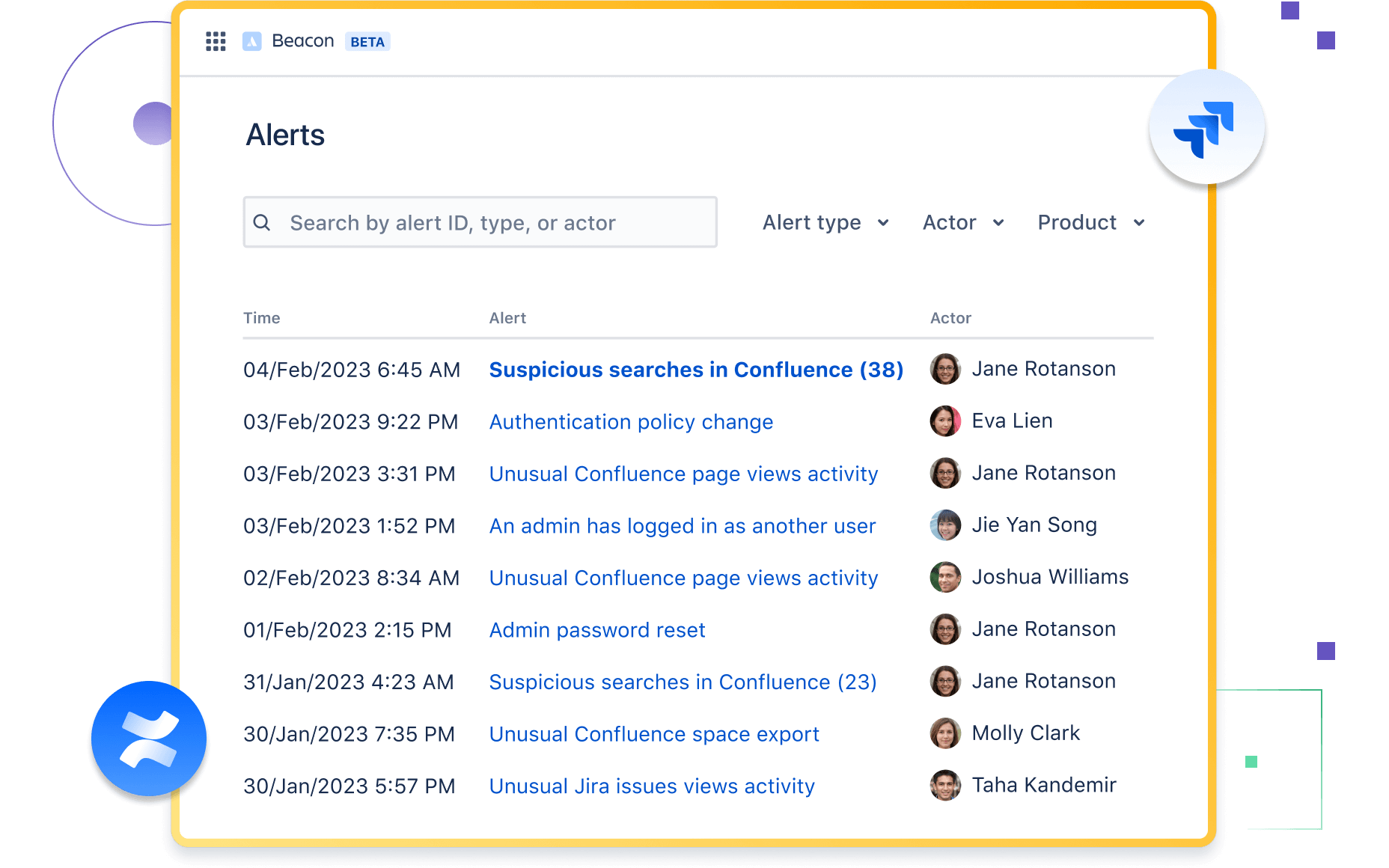
Beacon Intelligent threat detection for Atlassian products

GSPBC-1036: Defense Evasion - Indirect Command Execution - GuardSight, Cybersecurity as a Service
Understanding HP Wolf Identity/Credential Protection

Insider Threat Detection Recommendations

Your IT Security and Access Control Checklist

Chapter 7 Activity: Testing and Monitoring Security
de
por adulto (o preço varia de acordo com o tamanho do grupo)