Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Descrição
Describing activities of a crime group attacking Ukraine.
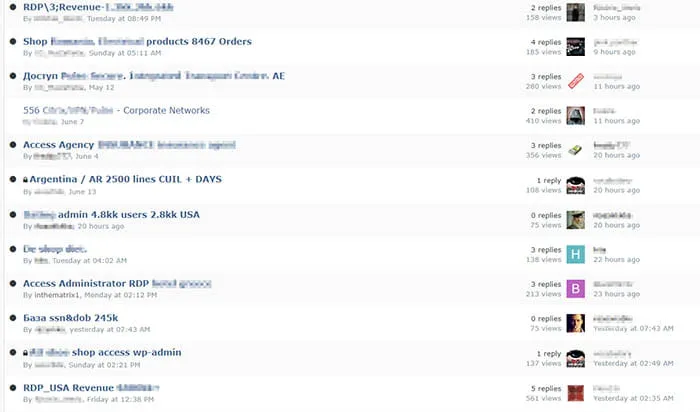
Initial Access Brokers Fueling Ransomware
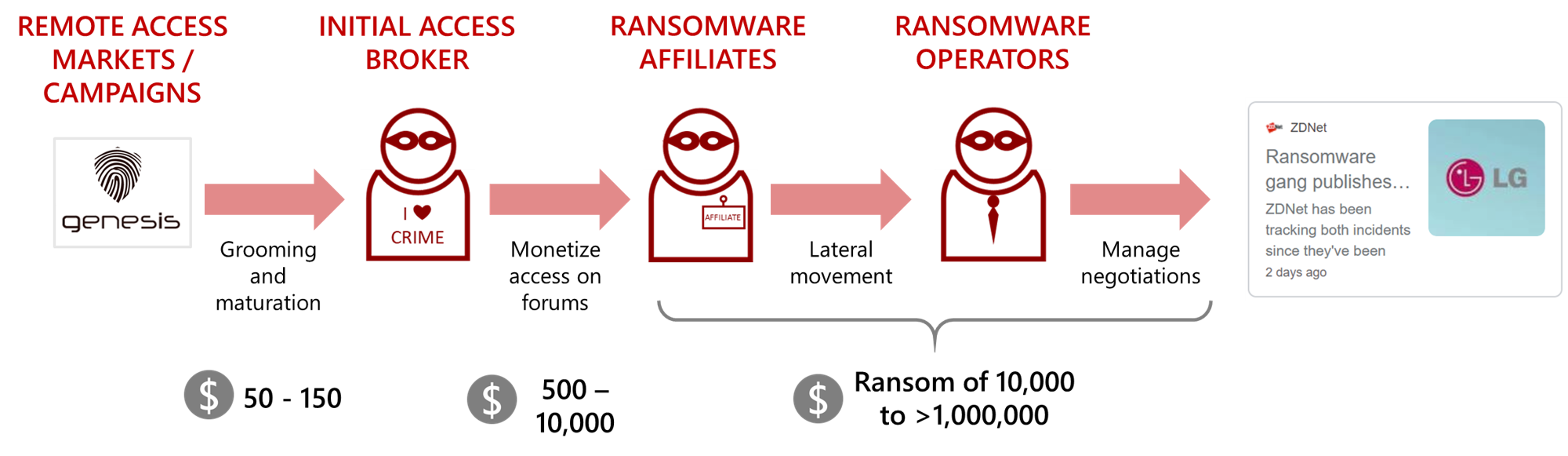
The Secret Life of an Initial Access Broker • KELA Cyber Threat Intelligence

Threat Trends: DNS Security, Part 1 - Storcom, Lombard, Illinois, United States of America

Initial access brokers: How are IABs related to the rise in ransomware attacks?

Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat
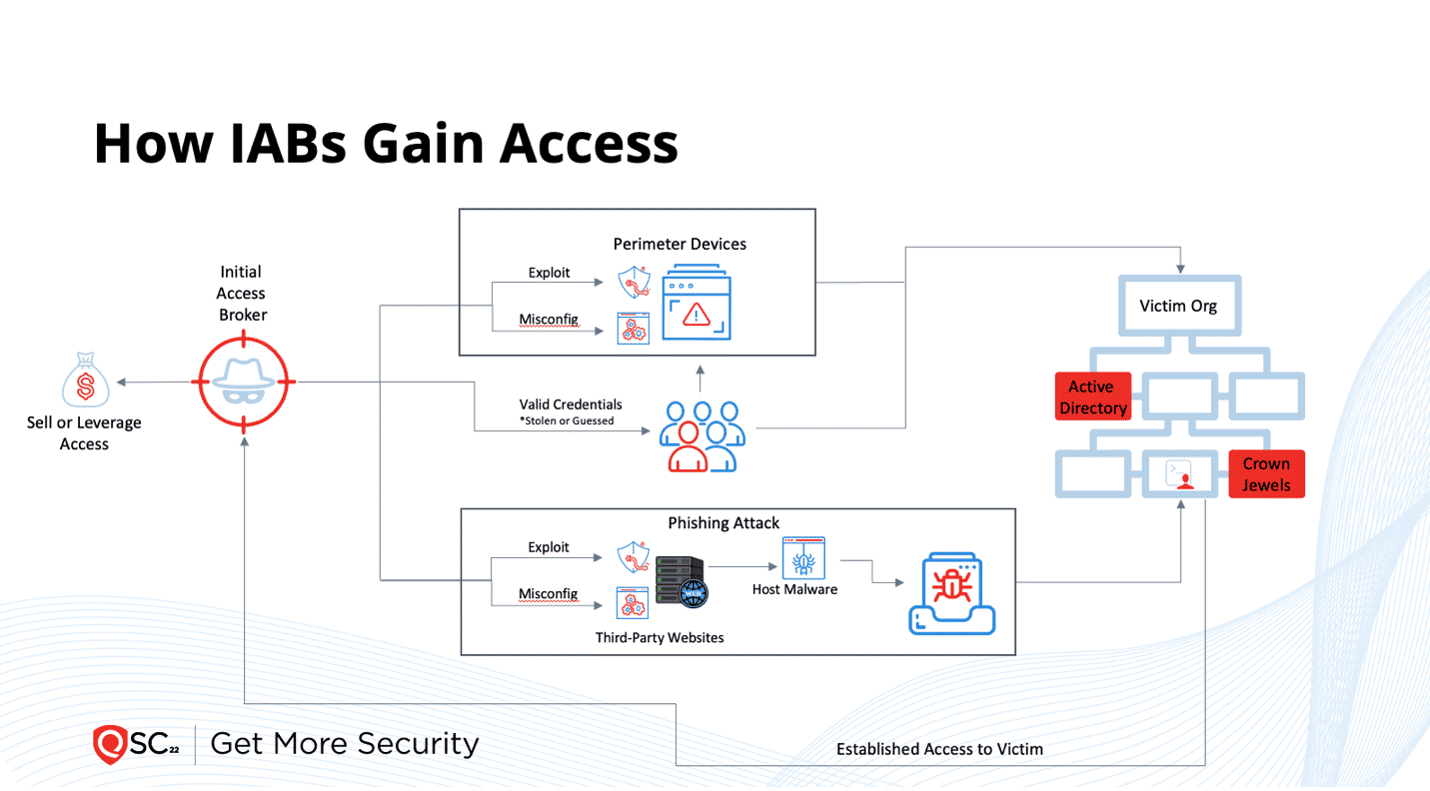
Cybersecurity Risk Fact #3: Initial Access Brokers Attack What Organizations Ignore
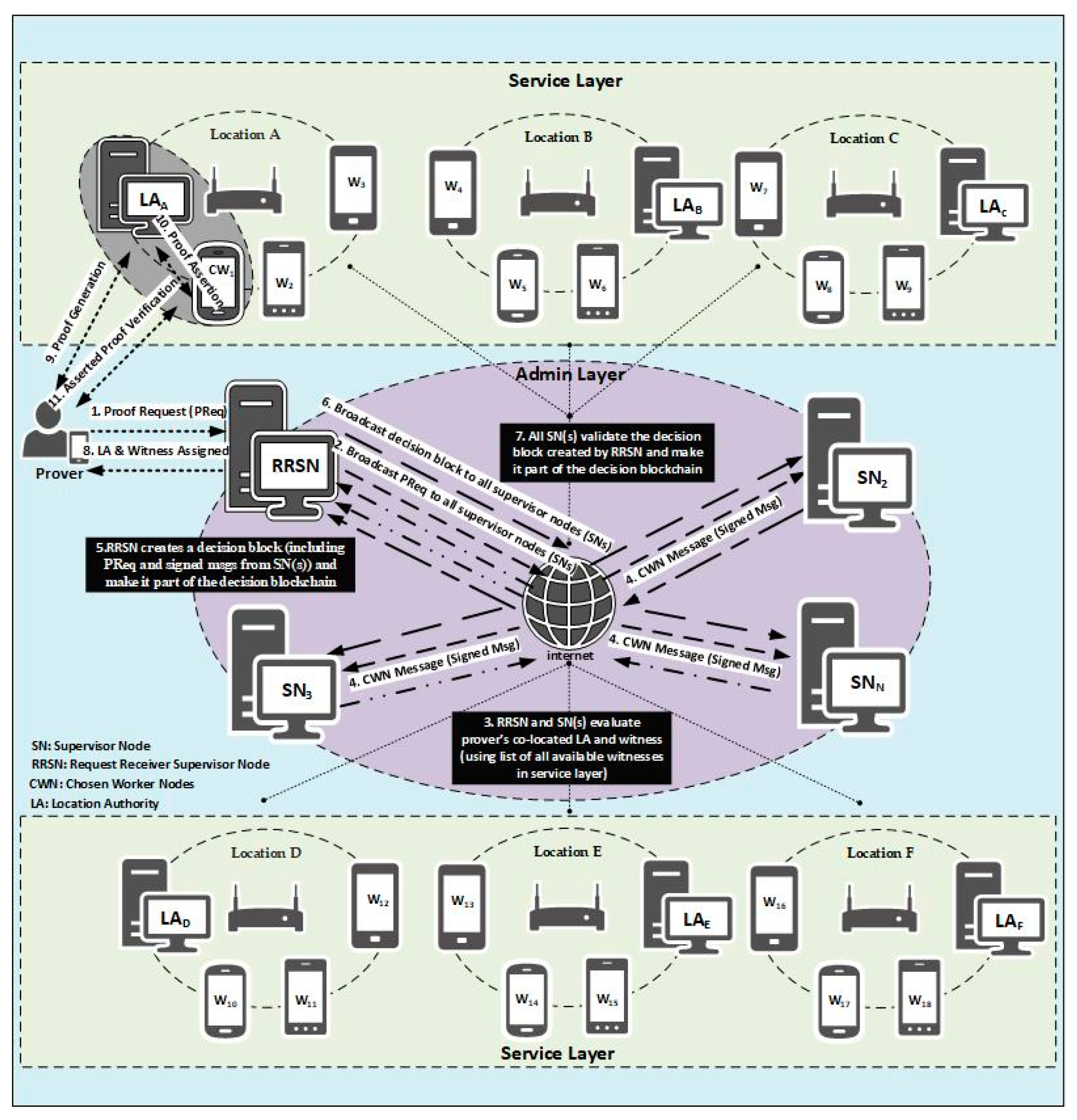
Sensors, Free Full-Text
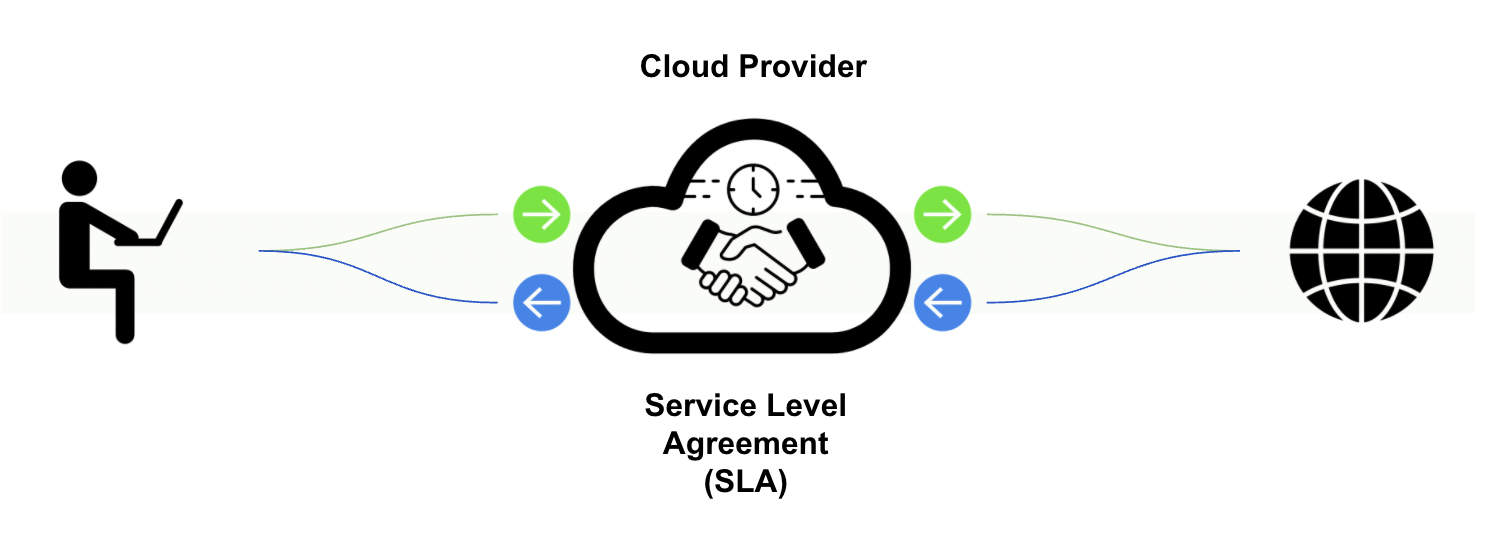
A Guide to Demystifying Cloud Security SLAs
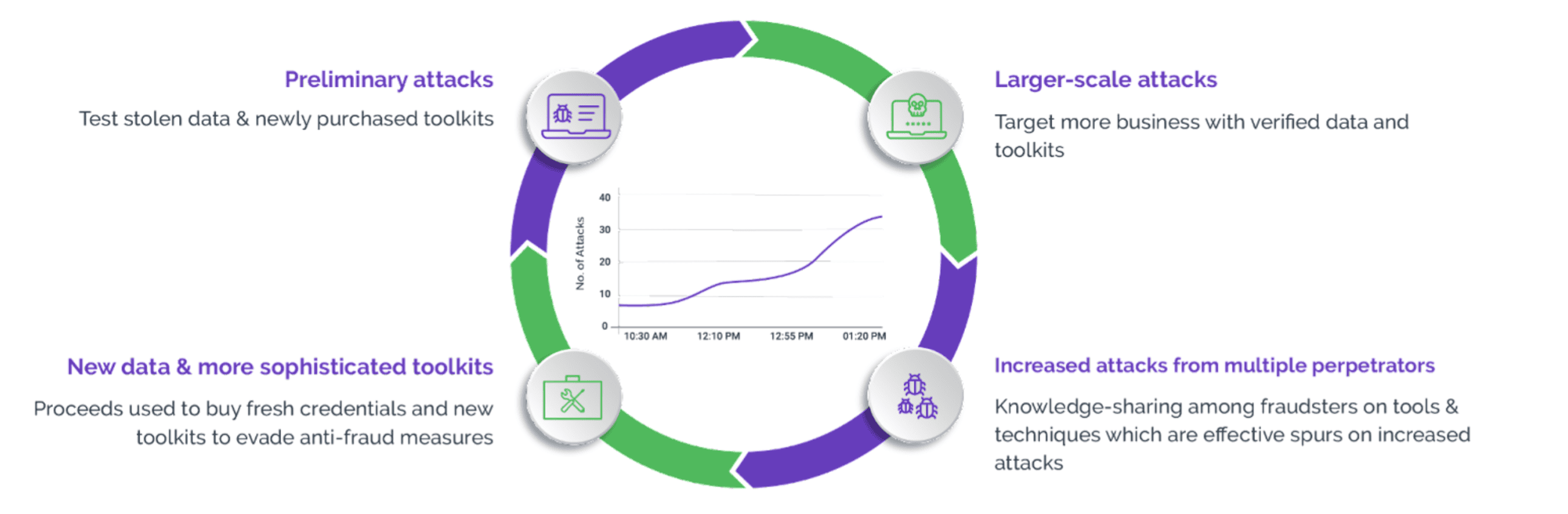
Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat

⚖️ LWIL #25: Copyright Claims Board, Algorithm Lawsuits, Location Data Rules and More

FBI, CISA and HHS warns of Royal ransomware gang attacks

So long and thanks for all the 0day, NCC Group Research Blog

Typical steps of APT attack Download Scientific Diagram
de
por adulto (o preço varia de acordo com o tamanho do grupo)




/media/movies/covers/2014/07/sword-art-online-2a-temporada_t91903_3.jpg)
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2021/k/t/afHNyZR8CvRi6aruIITQ/2015-09-29-ark-dinossauro.jpg)

